Introduction
You may have heard about digital signatures!
Or you may inform about providing e-government services with digital signature!
Certainly you know the tax operation in the electronic system of Taxation and Finance department along with digital signature?
Are you one of those people who doubt about security of computer systems that is necessary for each organization today?
Certainly, you’ve heard about the forgery of electronic documents in the virtual world.
You may have faced with difficulty of maintaining username and password!
Are you afraid of divulging username and password and abusing them by malicious people?
Certainly, you are sure about sensitivity of your financial information! So, how do you trust unsafe accounting systems?
The organization management part’s concern about content of electronic letters and documents in archive and even unauthorized access to confidential documents is a serious concern.
Do you know that you can guard your electronic letters easily against others’ access and aggression?
It may happen in your organization that a user is unaware falsely about the existence of a document in the system with its name!
Or even he denies it!
Did you know that access to confidential data at network level is very easy?
You may be one of those software developers whose customers always criticize the security of your software systems and so, lose some of your customers!
And you may search an easy and convenient solution to implement encryption function and digital signature at your software and system?
Now announce you, Keya3 Token fulfills all these needs and concerns. Keya3 Token is a product that was designed and produced by Iranian experts. This product provides easy solutions to assure about current permeable and unsafe computer systems by using new and modern cryptography technologies and digital signatures as well as utilizing its multiple programming tools and libraries.
Features
General features
- Fast data transfer by using type A of USB1.1 standard
- Low power consumption
- Secure internal memory until 256 KB volume and powerful system file
- A core accordance with smart card standard (ISO 7816) and supporting a wide range of smart card commands
- Automatic identification by computer without the need for driver (by using HID interface)
- Unique 64-bit serial number
- The ability to run in Windows and Linux environments.
- Usability in Dastine PKE middleware (Dastine-Enabled)
- The ability to write the contents of a virtual CD by using proprietary tools of token from client organizations.
Security mechanisms
- One-factor and two-factor accuracy verification with password key located on the software code or Personal Identification Number (PIN)
- Using PIN with maximum length of 32 characters for more security
- The ability to use cipher algorithms with maximum key length of 64 bits
- Implementation of all symmetric and asymmetric encryption algorithms in form on-board
- 3DES, DES, AES(128-256) standard symmetric cipher algorithms and PAYAM PARDAZ proprietary algorithm (PAYA2)
- The ability to use cipher algorithms according to customer order
- Asymmetric cipher algorithm (RSA 512-4096) for cryptography or digital signature purpose
- Generating the key pair (RSA 512-4096) inside module in form of on board
- CRC32, MD5, SHA256, SHA1 Hash algorithms and the accuracy of HMAC
- Encryption ability by unreadable key with injection service
- Possibility of defining key with different access levels (free, shared or private keys)
- Usability as hardware random number generator
Protection features
Using unique PIN key for internal memory password of each module
Using standard and exclusive secure protocol in order to protect exchanged and stored data (Secure Messaging)
Mechanisms of prevention of imaginable attacks to data module based on cryptographic techniques to maximize data security by micro manufacturer or the manufacturer of Tokens (Payam Pardaz Co.)
Using a hardware random number generator for internal requirements
Life cycle system derived from Life cycle of smart card standards including different phases (Manufacturer, developer, organization admin and user) and full control of information for each phase by phase owners
Use termination phase in order to phase out the module and destroy all information in emergency cases
Standards
- ISO 7816-4,8,9 smart card standards
- CSP (Microsoft CAPI)
- PKCS# 1,11,12
- Managing X.509 certificate
- PC/SC card reader driver
Applications
- Secure storage of sensitive data
- Hardware lock in computer programs to curb the illegal proliferation
- Hardware encoding in order to implement confidentiality service of computer applications
- Implementation of user’s accuracy verification service at computer applications
- Usability as a security token at PKI-based applications compatible with PKCS#11, CSP standards
- Secure Email transfer in Microsoft Outlook, Mozilla Thunderbird and Netscape
- SSL enforcement in IE and Firefox
- Application development based on PKI
- Application development based on smart card standard
- Smart card functions in Windows
- Two-factor login at Domain
- VPN enforcement based on digital certificate
Module affiliations
- Module library in Windows containing two programming interfaces , smart card and Token, it is supported directly at C and C++ and through COM interface in C#, Delphi, …
- CSP and PKCS#11 interfaces in order to introduce Keya3 as a secure Token in standard applications
- Storage certificate portfolio based on PKCS#12
- Necessary drivers and modules to be recognized as smart card in Windows
- Management and implementation software of Keya3 module
- Small applications in order to observe briefly all module capabilities (called Demo)
- Manuals and sample programs for programmers familiarity
Hardware Lock
An overview
Keya2 is a hardware module which was designed to increase security level in different computer applications. This module connects to computer through USB port and provides necessary secure services of application programs as a complete “plug & Play” solution. Keya2 is offered generally as Dongle (H and N models) and Token (W and T). Keya in form of Dongle often is used for cryptography of low volume data and protection software against piracy compact. Keya in form of Token can be used as accuracy verification module if it benefits from possibility of receiving PIN.
Some important security services of Keya 3 Token are as follow:
- confidentiality services
- Accuracy or integrity
- accuracy verification
General attributes
- USB 1.0 standard
- Low power consumption
- Automatic identification by computer as Plug & Play
- Using AES block cipher algorithms compatible with FIPS-197 standard
- Encryption ability by unreadable key in injection service (KV)
- Encryption ability by desire keys
- The ability to define Query (one-way function) for locking
- Using security protocols to protect exchanged and stored information in the module
- The ability to specify reading and writing access separately by programmer
- Secure connection between the application and module to deal with attacks (Cracking)
- Module ID and unique PIN key for each module
- The ability to use at Windows and Linux
Memory division into three sections and ranking access level of each section
- Secure Developer Memory
- Secure User Memory
- Free Memory
Unique attributes
- Usability of the modules in network (N model)
- Keya activation by receiving PIN from user (W, T and NW models)
- Equipped with Master PIN with the ability to define (W, T and NW models)
Applications
- Secure storage of sensitive data, up to 64 KB volume
- Hardware lock at computer applications to protect unauthorized proliferation
- Hardware encoding for privacy service implementation in computer applications
- User accuracy verification in computer applications (Token models)
Module affiliations
- Software kits in order to use module facilities in programming environments under Windows such as C++, C#, Delphi, Visual Basic, VB.NET and Java.
- Software kits and tools in order to use module at network (N and NW models)
- Library of using Keya in C++ language in user and Kernel models in Linux
- Storage software of certificate based on PKCS#12 standard (Token model)
- A software to identify as smart card in Windows (Token Model)
- Management and Program software of Keya module
- Providing free security applications such as Keyan software to enter safely into windows and PASS software as a file encoder (W model)
- Manuals and sample programs for programmer familiarity
Digital Signatue
At our world, no letter is valid without a signature, but each signature is not reliable, too. In traditional world, each person marks a written text on a paper by a sign such as a signature, seal or fingerprint to verify that text, otherwise it won’t be approved. In recent years due to advances in information technology, we have seen change of letter and paper documents’ styles into electronic documents and files that are created and processed by various organizations and software. We need a mechanism similar to traditional signature in cyberspace to validate this type of documents. Since computers and smart machines of electronic world know nothing except numbers; this type of signature must also be in the form of numbers but in a way that isn’t available to someone other than one’s own. Digital signatures is a cryptographic technique based on asymmetric cryptography as well as using asymmetric keys that converts connections, documents and generally all data into code according to signature owner’s request. Unlike traditional signatures, this sign nor has the appearance neither is visible, but it is a bit string of ones and zeros and can be validated by software and system. Digital signature is able to offer some tasks such as authentication, document verification and non-repudiation. Digital signature indicates that the apparent sender is the very original sender; however, in the electronic world like the real world, there is the possibility of fraud. Suppose, an email is sent from a seller to a manufacturer in which a large number of manufacturer products is requested. Now, buyer can’t accept this letter accuracy without reliable sign of manufacturer, also after a while, he can deny sending the letter. To use digital signs, we need a foreign central called CA (certificate authority) to verify the person’s name, software or site. After qualification verification, a digital signature certificate is issued for applicant. For example, electronic exchange sites, such as virtual stores, guarantee accuracy and reliability of exchanges for clients because they have this certificate. This certificate which has all characteristics of the certifier, date of issue and expiry date confirms the accuracy of exchanges; however, buyers also must obey security issues such as enough knowledge about Certifier Company, contacting to that company, if necessary and earning some information about the accuracy of issued certificate.
How does this signature work?
Digital signature methods are based on an encoding and according to asymmetric keys and hash. Asymmetric encoding uses public and private keys. It should be noted that each key is a set of numbers and characters. A public key is a key that is sent along with information to other party and he can have this key, but private key should never be given to anyone, somehow it is your password and used to encode information during connection to a specific person.
In fact, the unique series of numbers and letters is confirmed when a key is verified. This verification was placed at attachment of certificate. During the selection a key over a key ring, the certificate (license) of key can be observed and as previously mentioned, the time of this certificate validity and other parameters, such as name of person for who it was issued also are stated in it. Algorithms which are using for this purpose are so various, but RSA and Elgamal cipher algorithms and SHA, 5MD and hashing algorithms are the most common and widely used ones.
Iranian model of electronic security
In our country, many actions have been done by universities, government agencies and private firms in order to achieve e-government and the urgent need of this sector for security, both in public sector and admin affairs such as automation and e-commerce. Recently, root certificate authority center of our country has attempted to issue certificate for applicants of electronic certificates and digital signature mechanisms. In this regard, Payam Pardaz Engineering Co. has attempted in recent years to design and construct Keya3 Token which supports completely the digital sign mechanism and private key maintenance in a secure manner. It also can be used in different systems.
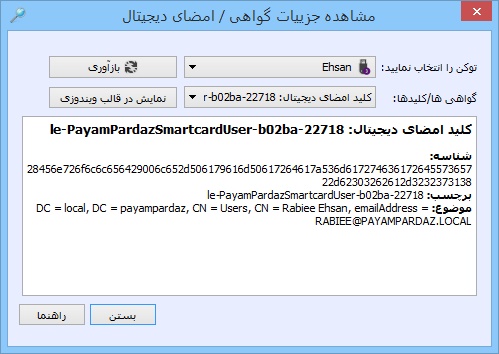
Screenshots