

Introduction to Keyhan
Dear Iranian managers of governmental and private organizations,
How much do you pay or attempt to keep your organization’s fundamental information confidential?
Have you ever taken necessary measures into account to make your computer networks extremely safe?
Have you ever implement an easy but complete solution to gain remote access to servers within the organization?
Today, information are supposed as main asset of individuals, companies and governments; so, it is predicted that in the near future, powers of government will be calculated on the basis of their information from individuals and organizations. It is clear that the value of organization information is greater than personal information. On the other hand, strategic situation and nature of Iran has always attracted the attention of strangers; so that the important Iranian companies, including oil companies are faced to the highest number of cyber-attacks (successful or unsuccessful). Now, the important question is that: in these circumstances, how much do our organization managers pay as or attempt to keep your organization’s fundamental information confidential? Have they ever taken necessary measures into account to make their computer networks extremely safe? Have they implemented security standards such as ISO 27001 at their organization?
Fortunately, in recent years, high-level managers have had more attention at the issue of securing their organization and computer networks insofar a strong improvement is observed at security level of organizations. But still, there are other unanswered questions. For example, aren’t our organizations at risk anymore? Has statistics of successful influential and attacks to our organizations’ computer networks decreased in recent years? How can we be sure that these solutions which provide security have necessary and sufficient efficiency? Don’t products that are using for ensuring security, have covert channels to influence and extract our organizational information? And finally, can we generally trust in foreign supplier in the field of security?
Payam Pardaz Co. with more than two decades of experience in the field of information security and connections as well as their local products’ portfolio can help you, dear manager, so much to find above questions’ answer. LAN-secure product of this company with KEYHAN brand name is the only domestic product which can completely cover applying two paragraphs of ISO 27001 security standard in your organization. This product with its local hardware security protocols, algorithms and Tokens can promote largely security level of your organization’s computer network and with proper use of it you can be sure about impossibility of covert channels’ utilization.
The auxiliary role of Keyhan product to implement ISO 27001 security standard are as follow:
Network access control
Usage policy of network service
User authentication for external connections
Separation of the networks
Network connection control
Controlling the access to OS
User identification and authentication
Expiration of session deadline
Limiting the time of connection
Isolating the remote sensitive systems
Correct processing of applications
Verification of input data
Message integrity
Keyhan properties and features
Today with the development of information technology, all large and small organizations with either LAN or WAN computer networks are all in a vast geographical area. The organization servers are usually located in the network center and applications on client computers receive necessary service from these servers. Alongside development of technology, threats and cyber-attacks become more widespread and some attacks such as access to data through network or stealing password and role playing may happen. Thus, providing security of electronic services has recently become one of the most important issues that IT managers of organization is facing.
On the other hand, special-purpose attacks which was carried out recently against important sections of Iranian installations have led IT managers’ attention to focus on provision of their organization’s server security and sensitive data more than before.
Keyhan which is a domestic system to make network safe provides obviously different security services such as users’ two-factor authentication, access control, confidentiality and accuracy of transferred information, traffic analysis and high availability. Keyhan can significantly help to implement famous security standards such as ISO 27001 by its local hardware security protocols, algorithms and Tokens. This system contains a server (to apply in the entrance of organization’s sensitive servers), client software (for users’ computers), management software and hardware security tokens of users (with Keya brand name), it can be launched easily at organization network as well as utilize without the need for special training.
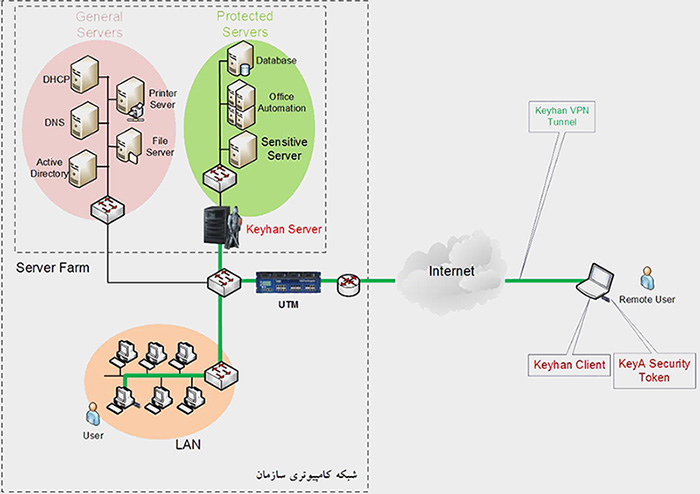
Applications
- Securing applications under organization network such as office automation
- Providing safe connection among computers in an organization representative offices and servers of headquarter
- Safe connection to organization servers by remote users (secure telework process)
- Making a safe connection among clients’ remote desktop and their private servers in data centers
- Possibility of creating an isolated and secure virtual network (VLAN) for sensitive sectors of an organization such as Security department
- Making a safe connection among users’ computers and centralized management or distributed management
- Provision security of wireless network platforms
Security features
- Confidentiality and accuracy of transferred data based on a specific Tunneling protocol at the network layer
- Mutual authentications (user for server as well as server for user) based on a private protocol
- Two-factor user authentications by using Keya domestic security Token (made by Payam Pardaz Co.)
- The possibility of user authentications based on PKI platform
- User access control and preventing intrusion to network of servers under protection of dedicated firewall
- Possibility of defining a secure virtual LAN as centralized and distributed ones
- Tunneling protocols’ security and authentication based on symmetric cipher algorithms with a 256-bit key length
- Using cipher algorithms and standard and domestic accuracy (it can be ordered by customer)
Network attributes
- Clear performance form users and servers’ point of view (No need to change applications and server configurations in network)
- Supporting NAT[1] (user connection by an invalid IP) and PAT[2] (placing servers at DMZ[3] area)
- Ability to provide Single Sign On (SSO) to application layer and strengthening user authentications mechanism
- Low overhead traffic than other similar security protocols at the network layer (like IPsec)
- High availability and resistance against any damage with the ability to distribute the load on Keyhan multiple servers
Management characteristics
- Ability to classify security policies and users
- Ability to define security policies and access control rules for each user or other user groups separately
- Ability to determine time for user groups
- Ability to limit a user to work on a particular computer or a range of IP addresses
- Event logs of user entry and exit time, administrator transactions in the database, etc.
- The ability to send events to Syslog server based on RFC 3164 standard
- The ability to define middle managers with the controlled capabilities
- The ability to receive user information from active directory servers
- The ability to automatic synchronization among Keyhan redundant servers
Analytical reports of users’ access
- A report about the user access details to servers under Keyhan protection with details about minutes/hour/day and the possibility of filtering the users
- A report about the access volume to servers under Keyhan protection by users with details about minutes/hour/day
- A report of top 10 users who transferred the most traffic volume with server under protection process
- A report of top 10 servers to which the most traffic volume is transferred
- A report of total amount of used bandwidth of system
- A report of the most frequently used protocols and ports of system
- Export of all observed charts and tables at software in Excel and pdf formats
- Export of database with CSV format
Adaptability
- To Support Windows 2000, Xp, 2003 server, Vista, server 2008, 7, server 2008 R2, 8, server 2012 OS (all 32 and 64 bit versions)
Keyhan Screenshot

نرمافزار کاربری کیهان

نرمافزار کاربری: پنجره برنامه کلاينت کيهان پس از انجام موفق Login

نرمافزار کاربری: ابزارهای عیبیابی جهت رفع مشکل ارتباطی کاربر با سرور

نرمافزار کاربری: ابزارهای عیبیابی جهت رفع مشکل ارتباطی کاربر با سرور
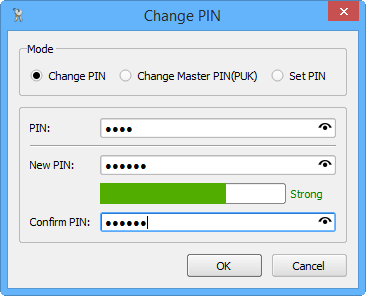
پنجره تغییر PIN ماژول کاربر
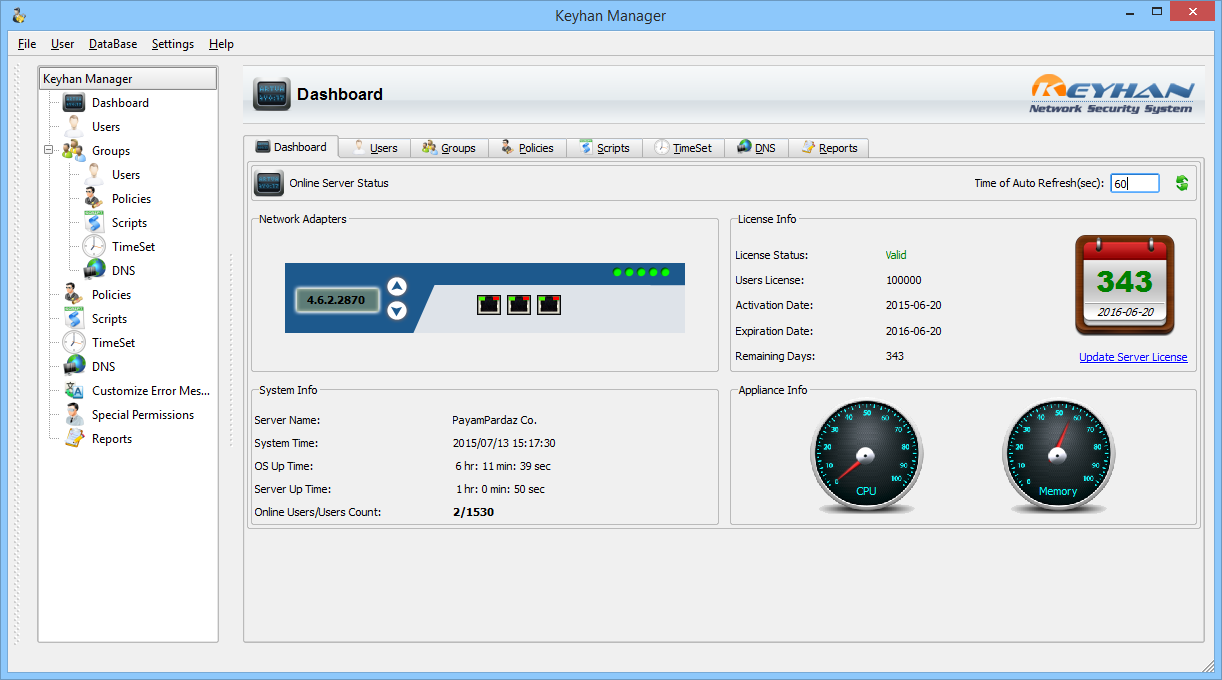
نمایی از داشبورد نرمافزار مدیریت

نرمافزار مدیریت: تعریف کاربر جدید
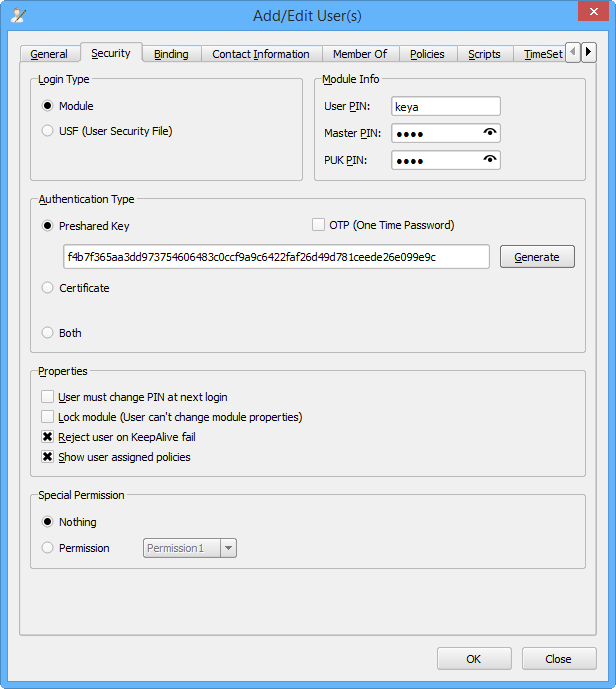
نرمافزار مدیریت: تعریف کاربر جدید

نرمافزار مدیریت: مدیریت گروههای کاربری
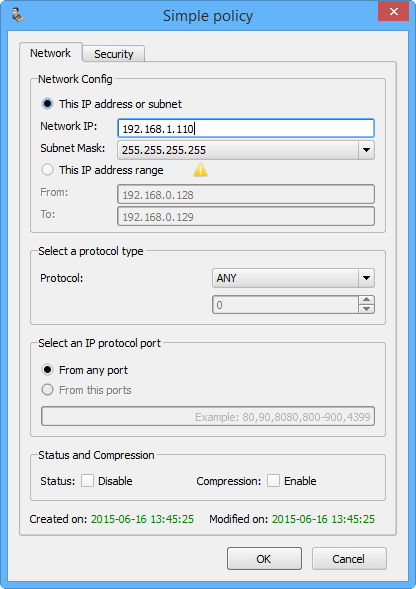
نرمافزار مدیریت: تعریف سیاست جدید جهت دسترسی به سرورهای تحت حفاظت

نرمافزار مدیریت: تعریف سیاست جدید جهت دسترسی به سرورهای تحت حفاظت

نرمافزار مدیریت: نمایش کاربران متصل به سامانه

نرمافزار مدیریت: پنجره تنظیم ویژگیهای امنیتی سامانه

نرمافزار مدیریت: پنجره مدیریت سرورها و بهروزرسانی خودکار نرمافزار کاربری
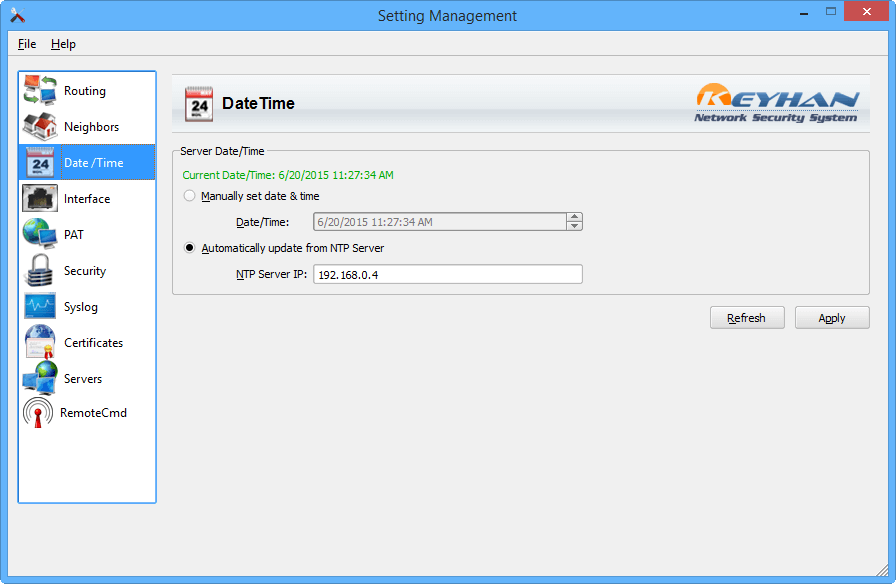
نرمافزار مدیریت: پنجره تنظیم تاریخ/ساعت سامانه
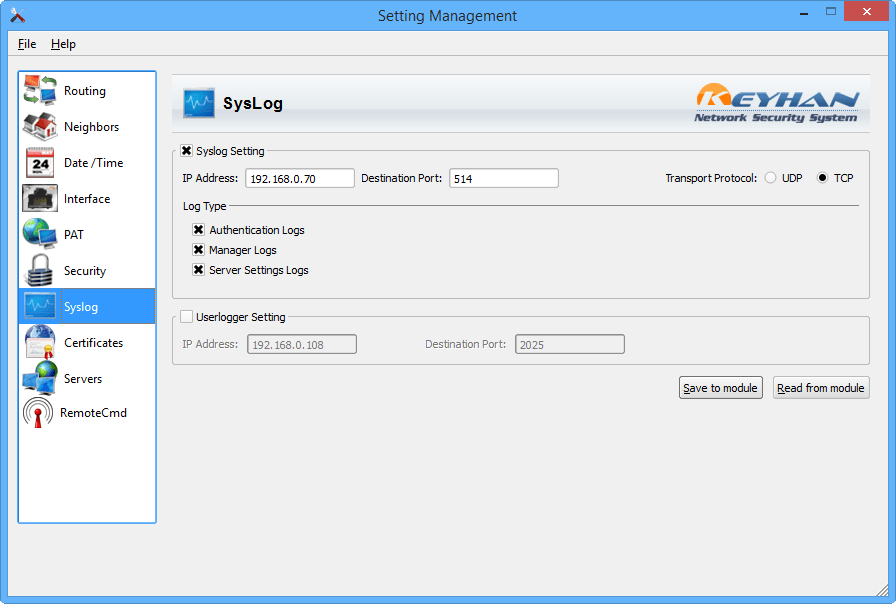
نرمافزار مدیریت: پنجره تنظیمات SysLog در سامانه
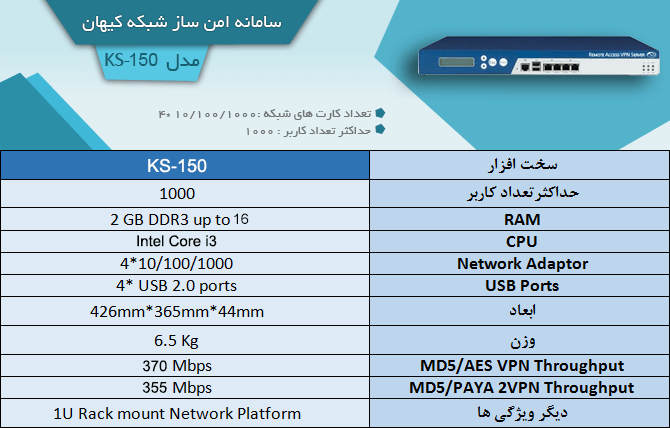
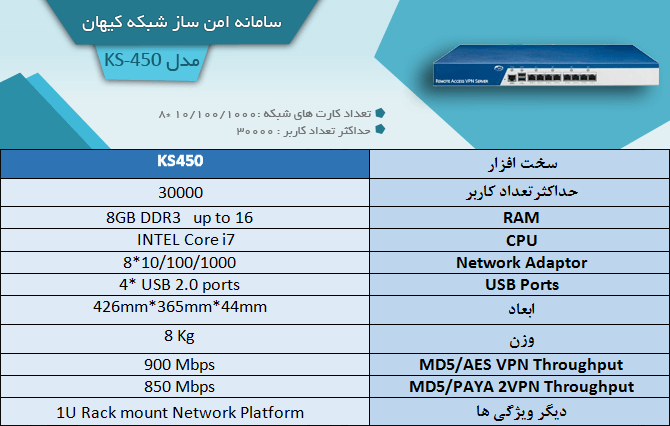
Models
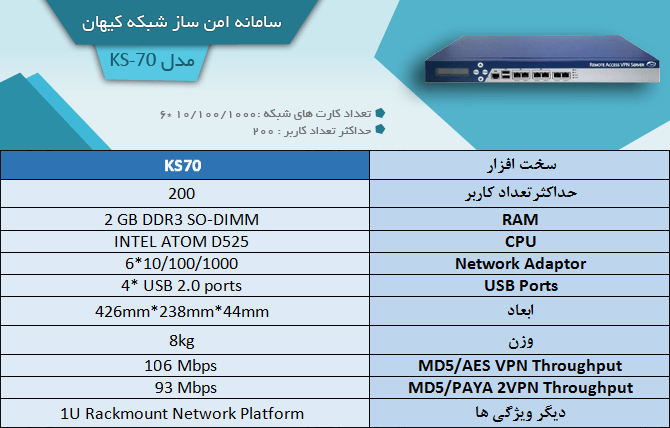

Traffic analysis system
Today, Keyhan system is used widely by different organizations of our country to secure the presentation of application services. In this system, Keyhan server as an input gate, plays a role to control the access to vital servers of organization. Since all packages which were transferred to protecting servers are permitted to login to protecting network after monitoring Keyhan server; this server can play a special monitoring role along with other core services to examine users’ activities and users’ accesses (including confidentiality, accuracy, authentication and two-factor access control).
Keyhan system reports completely all activities of this system in a proper format. These activities includes users’ status about connection to Keyhan and all system configuration changes or policies by admin. Details about done activities is reported in the form of an event which describes the status and results about doing that activity when user tries to connect to Keyhan system or a admin sets some settings up. A sample of these events are as follow:
- Status of users’ authentication (successful or unsuccessful)
- Unsuccessful login attempts to Keyhan
- Unusual logout of a user from the server
- A user’s logout by admin coercion
- User connection blocking
- Contradiction of user’s address with each other
- No support from user client version
- Viewing Keyhan repetitious user
- Network problems in connecting to Keyhan server
- Setting and policies changes of Keyhan by admin
After authentication for each user, user is allowed to access to protected servers. The passing traffic must be monitored from Keyhan to servers and this information is extracted from them to observe the status of connecting to servers, data transfer rate and success in connecting.
CA (Component architecture) of event management system and traffic analysis along with Keyhan system are shown in below figure. This system is placed between Keyhan server and protecting servers. It not only receives and protects Keyhan events, but also monitors traffic between servers and their users, extracts and maintains information about access process.
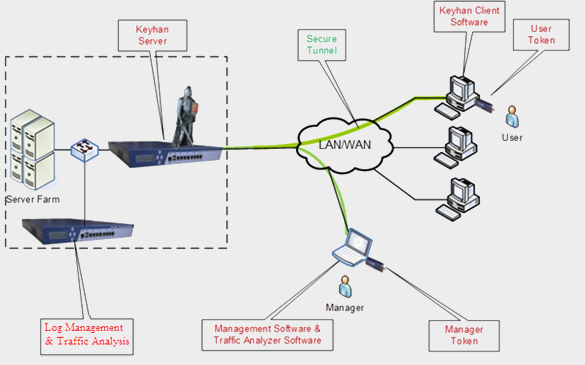
استقرار سيستم مدیریت رویداد و تحليل ترافيک در کنار سامانه کيهان

نماي داشبورد سیستم
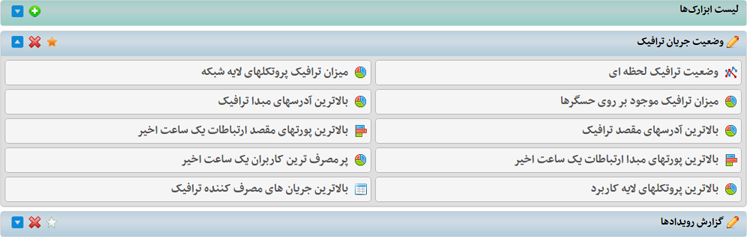
نمونه داشبورد مربوط به يک کاربر

لیست رویدادهای ذخیره شده
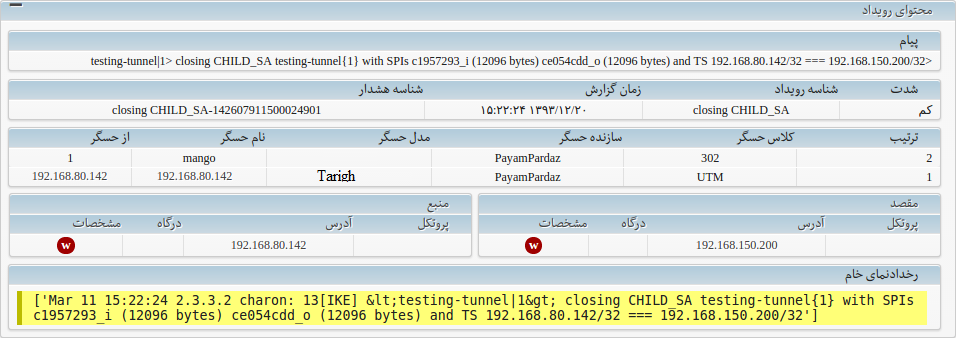
جزئیات رویداد خام و نرمال شده

گزارش اطلاعات جریانهای شبکه
List sample reports
Many reports can be defined from different transferred entrances. Also, a time schedule can be made to offer these reports. Reports are available on a periodic basis and in terms of hourly, daily, weekly and monthly schedule. Several parameters can also be defined and customized for each report. If you receive events; a part of sample report types is as follow:
- An Attempt to enter into a system
- An attempt to enter in the whole network unsuccessfully
- An attempt to enter in a system unsuccessfully
- Disablement of different network services
- Unsuccessful attempt to access to a file
- Changes in managing the users as well as deleting and adding them
- The most reported malicious traffic on the network
- The most reported malicious traffic in a system
- Most addresses from which events have been reported
- Most addresses that have been the target of various attacks
- Most malwares which have been reported in the organization
- Most malwares which are active on the network
- The highest types of attacks that did against organization assets
- Most resource types of services and systems that have been attacked
- Most outcomes that reported events and observed attacks have been on network assets
- Most configuration changes in various network systems
- A report about servers to which the most traffic is transferred
- A report about total amount of used bandwidth of system
- A report about protocols (at network and application layer) and the most useful ports of system
- The highest points of network that have been targeted an identification attack
- The highest invaders which did non-service attacks against network assets
- The most polluted network assets are the source distribution various malware
- The highest points of the network that are sending spam to mail servers
- The highest systems that have a background about working in Botnet
- The highest system that has transfer data as shared data on related protocols
- The highest data changes that have been reported in the database servers
- Most attacks have been reported on a specific port
- Most attacks have been reported against a particular service
- Most standard activity events in network
- Sensors that have reported the largest number of event
- Most ports on which traffic packages of network are thrown away
- Most ports that are used to distribute malware
- The most done attacks against web server in organization
- Most assets that search a domain name that suspects servers of domain name
- Most addresses from which abnormal traffic is reported
- The highest attacks that were done against network bandwidth
- The highest protocols on which different types of traffic that were covered by channel are transferred
- And ….
Securing system of users’ connections
Introduction
Today with the development of information technology, all large and small organizations have LAN computer networks in a narrow or wide space. Since parallel with the development of technology, threats and cyber-attacks become more widespread and possibility of some attacks such as data access on the network or infiltrates into the system as well as playing role simply; so, now provision of computer and non-computer systems’ security equipped with a network port has become one of the most important issues that IT managers of organizations are faced with.
Domestic Keyhan software which is used for provision of network security offers clearly various security services such as two-factor user accuracy verification, firewall, confidentiality and accuracy of transferred information. This system includes a client software (for users’ computers) plus hardware security Tokens. It can launch simply in network and utilize without the need for special training for users in order to make connections of users safe and control the accessibility of their systems in accordance with the considered policies of organization or system owner.
Areas of application
- Securing wireless and optical fiber connections among buildings of an organization.
- Securing connection between two subnets with each other in the organization.
- Establishing a secure virtual LAN (VLAN) in form of a software among users of an unified organization.
- Securing the connection among organizational sensitive servers with each other (databases).
- Using as a personal profile for users with central control and management and its synchronization with security policies of the organization.
- Isolating users’ system during working with sensitive servers (disconnecting all connections).
- Securing connection between computers and all non-computer equipment equipped with a network port such as camera, printer and… .
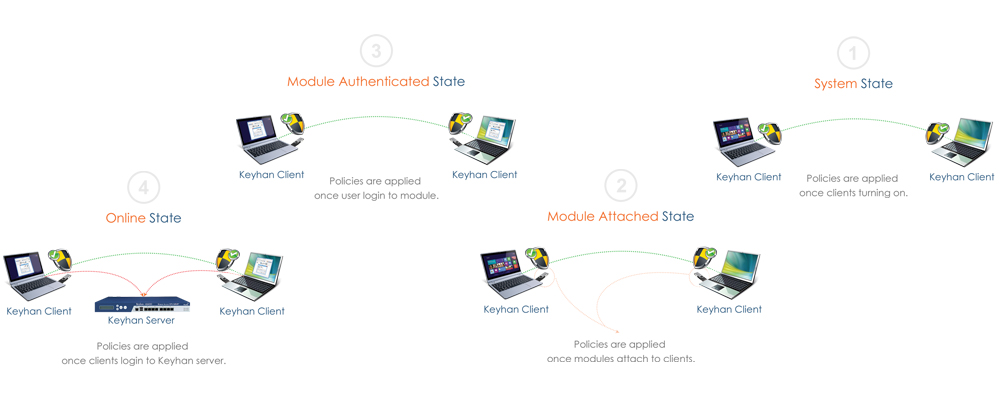
Diversity in definition of policies with different applications
- Systemic policies: policies that are applied in user’s system as soon as the computer is turned on.
- Modular policies- service mode: policies that are applied in user’s system as soon as module connects to computer.
- Modular policies- safe mode: policies that are applied in user’s system as soon as logins in module.
- Online policies: policies that are applied in user system as soon as user software connects to Keyhan system.
Application scenarios
First scenario
The aim of this scenario is securing the organization servers (for example, in this scenario, database server of organization is considered). In fir stage, all input and output connections are controlled by branch database (B database). To this end, firewall polices prevent the entry and establishment of all connections from WAN network. Also, access policy is defined just for users who are allowed to use this server in LAN network and unauthorized users are not allowed to access to LAN. If the servers or users located in branches and central servers of organization need a secure connection; we can make this connection by providing a proper and safe encrypted framework in WAN network. For example, a proper access is provided in this scenario to synchronize databases by providing a secure tunnel between database of branch and Keyhan server located in organization.

ویدئوی نحوه پیادهسازی سناریوی اول
Second scenario
such as internet, intranet, wireless and fiber optic. To provide a safe platform, we can use Keyhan Subnet to Subnet tunnel service. By using this tunnel, secure and encrypted platform is provided between two networks. Implementation of this scenario just needs to install Keyhan client software on two systems that are defined as gateway of the organization. This connection is established by defining network address range under protection and definition of considered accesses.
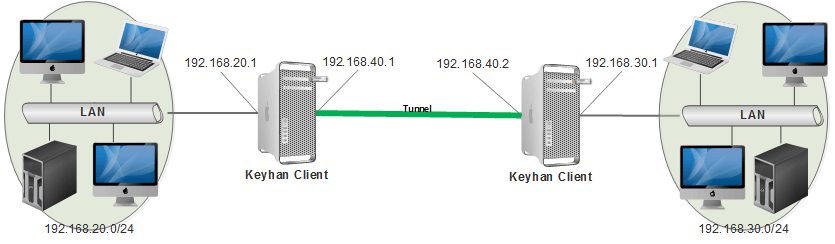
ویدئوی نحوه پیادهسازی سناریوی دوم
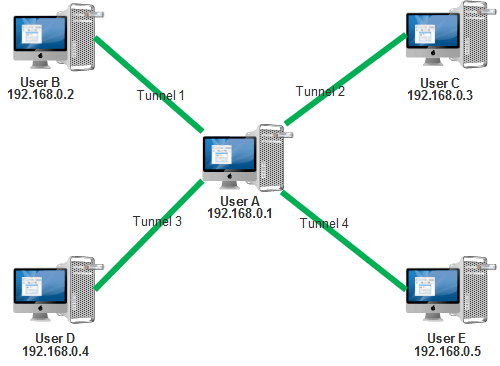
Third scenario
In this scenario, organization servers are protected by using Keyhan system. Users of network are classified. They access safely to sensitive servers of organization, based on their need. In this example, there is a database server in network that accesses to main database server for synchronization (Tunnel 2). Also, we can make a safe connection, if necessary, among users of system. In this example users work with internal database through safe connection (Tunnel 1).

ویدئوی نحوه پیادهسازی سناریوی سوم
Fourth scenario
in this scenario, the connection of one system is secured with other users by using Keyhan client software. In this example “A” user connection and other users is made by encrypted platforms. Also, it is possible to prevent entry or exit of unauthorized packages by defining considered access in firewall of this system.
ویدئوی نحوه پیادهسازی سناریوی چهارم
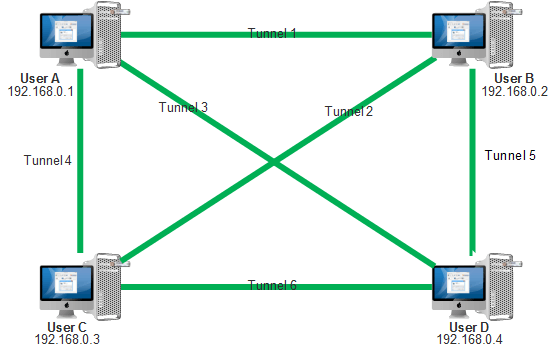
Fifth scenario
In this scenario, connections of all systems are secured with each other by using Keyhan client software.
ویدئوی نحوه پیادهسازی سناریوی پنجم
Downloads

